- Ensure that the application fails securely
- Ensure that error messages do not reveal sensitive information
- Ensure that system errors are never shown to users
- Ensure that resources are released and transactions are rolled back when there is an error
Sample Checklist: Logging
- Ensure that all user / system actions are logged
- Ensure that sensitive information is not logged (e.g. passwords)
- Ensure that Logging is enabled for user management events (e.g. password reset)
- Ensure that unusual active such as multiple login attempts are logged
- Ensure that logs have enough detail to reconstruct events for audit purposes
- Ensure that logging is highly configurable (logging levels)
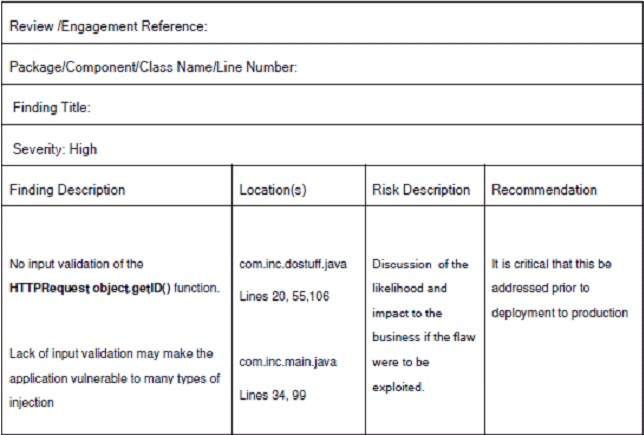
SAST Finding
- The SAST findings keep the development team informed about the findings gathered by the security team during the secure code review
- The findings generally include vulnerabilities, architectural problems, organization issues and any mismatch in the best practices followed The security team members may include the following features in the findings report:
– Select a meaningful title for the findings report: The title should be clear and should convey the details of the issue clearly to the development
– Determine clearly the location of the issue: The development team should easily identify the location of the issue from the report
– Provide detailed description of the security issues: The security team should include the following details regarding the following details regarding the security issue:
– A clear description about the vulnerability
– Analysis of the possible attack areas
– Description about the factors leading to the attack - Provide a description about the risk ratings: The risk rating enables the development team regarding the value assigned to each security issue found. The report may also contain the explanation behind assigning any particular value to an identified security issue that may enable the development team to understand the impact of the security issue at a glance. The commonly used risk ratings during code review are as follows:
– Critical
– High
– Moderate
– Low - The security team should follow some standards while assigning risk ratings to the security issues during secure code review
- Provide proper corrective measures to the development team: The security team after the secure code review may provide certain corrective measures that enable the development team to easily rectify the security issues. The rectification measures may also include:
– Other course of action
– Total amount of effort required for rectification
SAST Reprot
The SAST report consists of the following details:
- A list of vulnerabilities and its related details along with the severity level
- The rectification measures taken for controlling the vulnerabilities and errors found in the code
- Graphical representation of the security measures required for the application
- Control measures that can be taken for future security as well
SAST Reporting
- Report the findings of the code review in a structured way
- The report should include:
– Weakness Metadata
– Details of Place to find the issue
– Through Description
– Detailed description of the issue
– Recommendation
– Recommendation to mitigate the issue
– Assign appropriate Priority
– Give priority to the issue for the developer to prepare his to-do-list
SAMPLE REPORT
SQL INJECTION
Location: \myProject\UserModule\User.jsp?username=
Description: The code below builds a dynamic SQL statement without validating the input from request parameter. This may lead to SQL INJECTION
String query="select FirstName,LastName from Users WHERE UserName='" + request.getParameter("username") + "";
PreparedStatement stmt=con.prepareStatement(query);
ResultSet rs = stmt.executeQuery();Recommendation: Use parameterized SQL query; do not dynamically concatenate the request parameter value to the string query.
Ref: https://www.owasp.org/index.php/SQL_Injection_Prevention_Cheat_Sheet
SAST Reporting (Cont’d)
Finding Report Sample
Risk Rating

