- SAST, also known as secure code review, is one of the software security assurance approach to identify security-related weaknesses in the code
- It involves detailed systematic inspection of source code to detect vulnerabilities and design flaws
- It should be performed toward the end of the source code development when application code is stable or nearly completed
- It should always be performed in combination with human effort (Manual) and technology support (Automated)
Objectives of SAST
- SAST aims to detect application security vulnerabilities are their root cause when code is not running
Root cause analysis (Source to sink)
– Source to Sink analysis (what is the source (input) and the sink (vulnerable code pattern) for any vulnerability) is carried out using Data flow diagrams
Find all Instances of the Common Vulnerabilities
– Security code review enumerates all instances of certain vulnerability
Analyze Effectiveness of Existing Security Controls
– Security code review enumerates weakness in the existing security control against known threats
Design Analysis
– Design flaws like mishandling of nonuser inputs and external integrations like server-to-server can be easily identified
Identify Uncommon Security Flaws
– Security code review being specific to the application may highlight some flaws like insecure termination of execution flow, synchronization error, etc.
Effective Remediation Recommendations
– Suggests mitigation techniques that can best suit the application instead of a generic one.
Why SAST
- Many serious security vulnerabilities can be addressed
- Decreases the remediation cost of vulnerabilities in later stages
- Deeper analysis is possible with less false positive and negative
- Help you to add best secure coding practices as per department coding standards which can prevent future security issues
Skills Required for SAST
- Able to think from the attacker’s perspective
- Working knowledge of the programming language under review
- Knowledge of standard, secure coding techniques
- Quickly able to detect insecure coding practices
- Analytical skills
What to Look for in SAST
- Look for the code that implements common application security mechanisms
- The insecure implementation of security mechanisms can render applications vulnerable to various attacks
Common Application Security Mechanisms
- Authentication
- Authorization
- Session Management
- Data Validation
- Error Handling
- Logging
- Encryption
- Security Configuration
Common vulnerabilities Identified through SAST
- SQL Injection
- Cross-site Scripting
- Authentication Flaws
- Cryptographic Flaws
- Buffer Overflows
- Malicious File Execution
- Cross-site Request Forgery
- Sensitive Information Leakage
Types of SAST
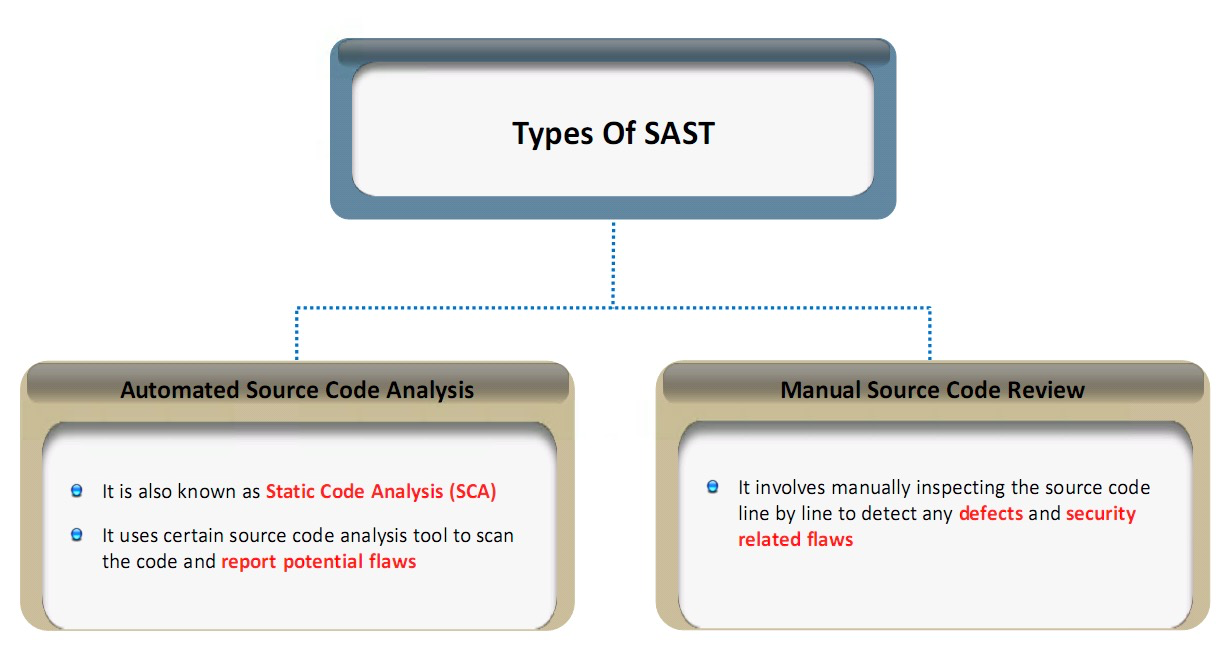
Automated Source Code Analysis
– It is also known as Static Code Analysis (SCA)
– It uses certain source code analysis tool to scan the code and report potential flaws
Manual Source Code Review
– It involves manually inspecting the source code line by line to detect any defects and security related flaws
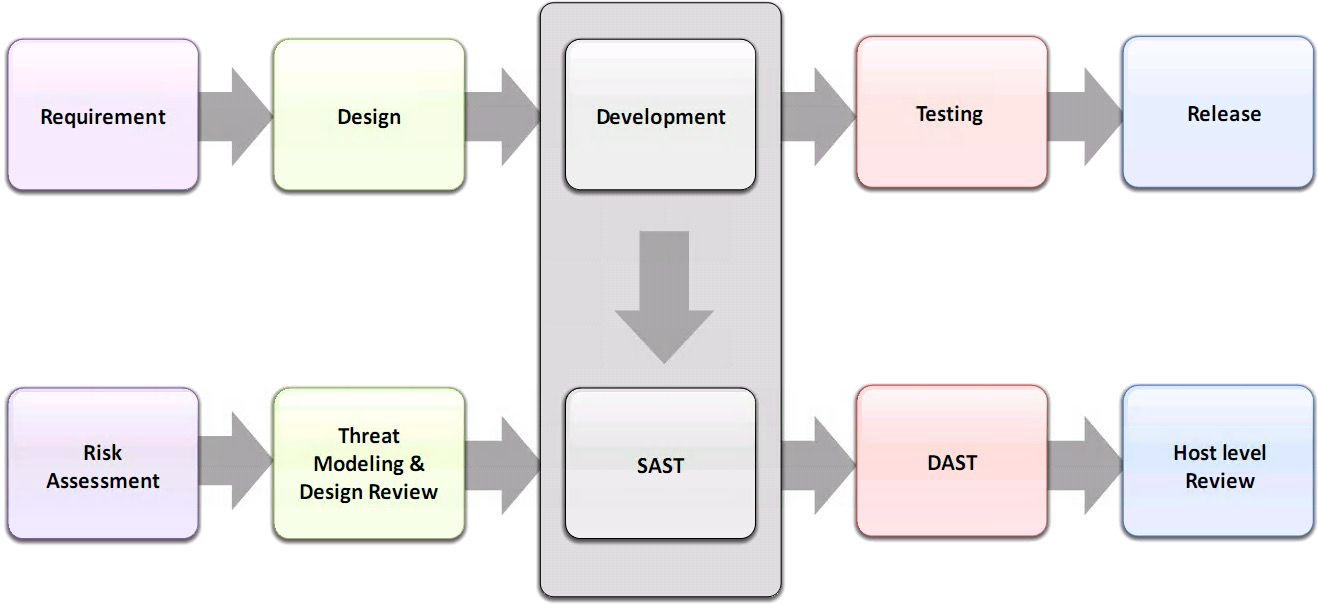
Where does SAST Fit in SDLC ?
SAST Steps
- Perform an application walkthrough
– Understand the applications functionality - Developers Interview
– Talk to developers; more you involve developers, more effective you secure code review will be
– It will help you quickly
– Determine the high risk areas
– Understand developer’s logic behind particular functionality
– Establish friendly and respectful relationship between you and developers - Analyze threat Model
– Figure out the major existing security threats - Define secure code review objectives
– Based on threat model analysis, identify the objectives such as:
– Code review for all major security vulnerabilities
– Code review for OWASP top 10
– Code review for specific vulnerability - Define scope for secure code review
– Be clear on what to look for and what to avoid
– Calculate the time and efforts required
– Define the budget constraints - Categorized the Objectives
– Prioritize the objective based on severity and requires more attention - Conduct Static Code Analysis
– Use multiple source code analysis tools to perform secure source code analysis
– Most common vulnerabilities and flaws are identified - Conduct Manual Source code Review
– Inspect the application’s code line by line in order to find the use of insecure coding practices - Remediation/Recommendation
– Suggest secure coding practice for each findings - Prepare Report

SAST Activities-flow Chart

