- Hashing is one of the forms of cryptography that transforms the information into a fixed-length value or key that represents the original information
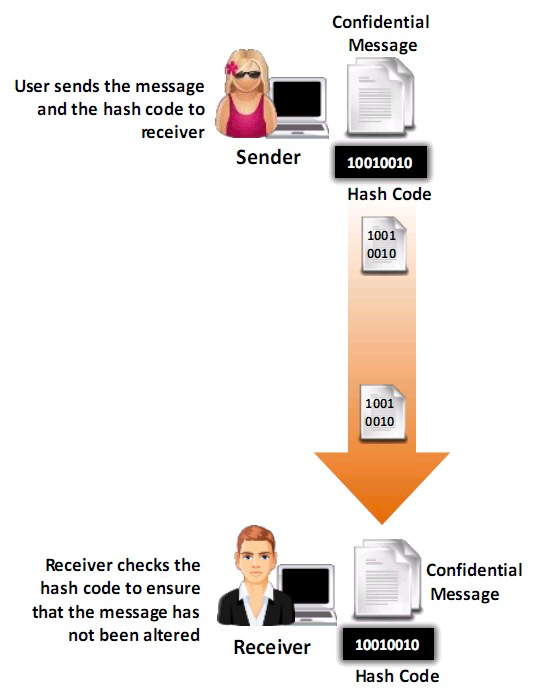
- The hashing technique ensures the security of information by checking the integrity of information on both the sender and receiver sides
- Checking the integrity of information
– The sender of the message creates a hash code of it and sends the message to the receiver along with its hash code
– The receiver again creates a hash code for the same messages at the receiver side and compares both the hash codes; if it is a match, then the message is not tampered in the transmission. If they do not match, then message is tampered with by third parties during transmission
Hashing Algorithms
- To implement hashing in Java include java.security.MessageDigest class
- MD2, MD5, SHA-1, SHA-265, SHA-384, SHA-512, PBKDF2, bcrypt, and scrypt are some of the hashing algorithms used
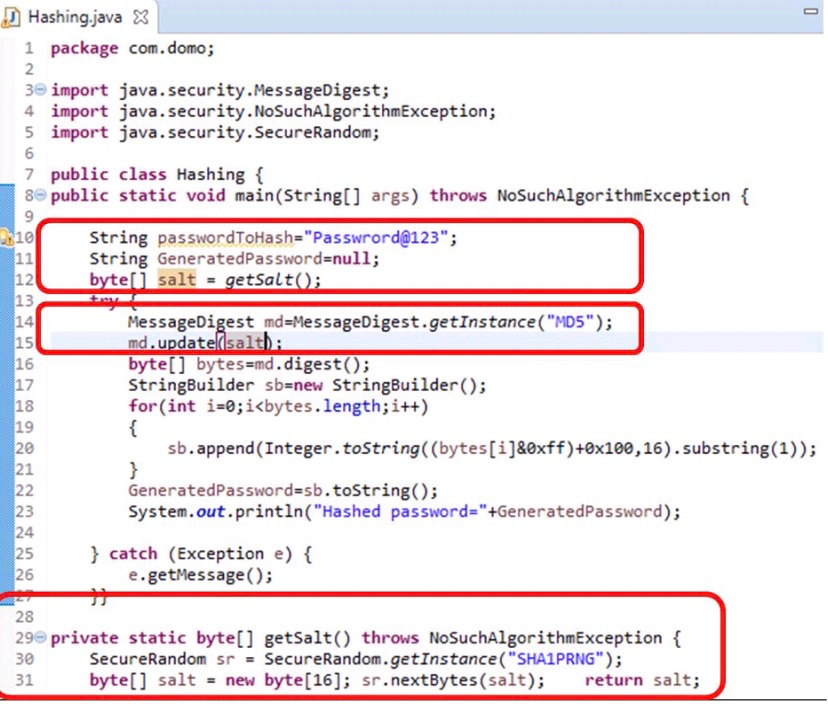
Example: Hashing using MD5

Securing Hashed Password with Salt
- Hashing the same password results in the same hash every time which makes it vulnerable to Dictionary and Brute Force Attacks
- Rainbow tables, lookup tables and reverse lookup tables are used to crack Hash codes
- By adding a random string (salt) before implementing hashing results in generating random hash for the same string (password)
Do’s and Don’ts while Implementing Salting
- Do not use hard-coded salt
- Re-Generate a unique salt each time
- Ensure that the size of the salt is big enough to generate numerous possible salts, so that the attacker cannot generate a Lookup table to crack the passwords
- Do not implement double hashing
Example: Implementing Salting before Hashing