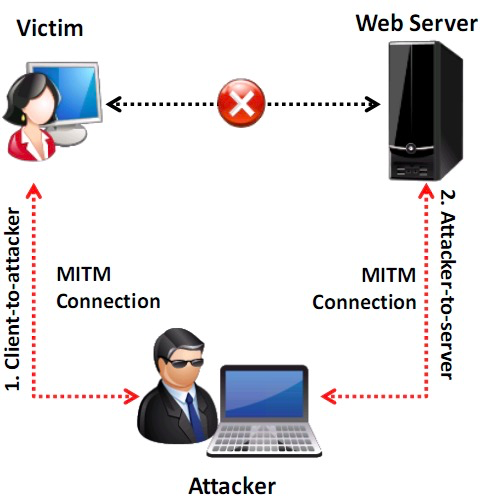
- Man-in-the-Middle (MITM) attacks allow an attacker to access sensitive information by intercepting and altering communications between an end-user and webservers
- For any data that travels across the network, there is a possibility of manipulation or modification of data by intruders
- If the data is not adequately encrypted using digital signatures or digital certificates then there is a possibility of data leakage
- The information that travels may contain personal data, credit card numbers and passwords
Digital Signatures
- Digital signatures are used for protecting and maintaining the integrity of digital data, downloads, the source of the message and a software license file
- JCA provides a specific framework for digital signatures with java.security.Signature class that provides the functionality of signing and verifying digital signatures
- The Signature class and signedObject class provide the basic functionality of digitally signing and verifying digital signatures in JCA

